Canonical
on 2 May 2018
For some time, we’ve wanted a mechanism to alert snap publishers to security updates which affect their snaps. All the pieces have come together and we are now sending alerts via email. Stated more precisely, publishers who use ‘stage-packages’ in their snapcraft.yaml will now be alerted when Ubuntu Security Notices (USNs) have been issued for their staged packages. An example report looks like this:
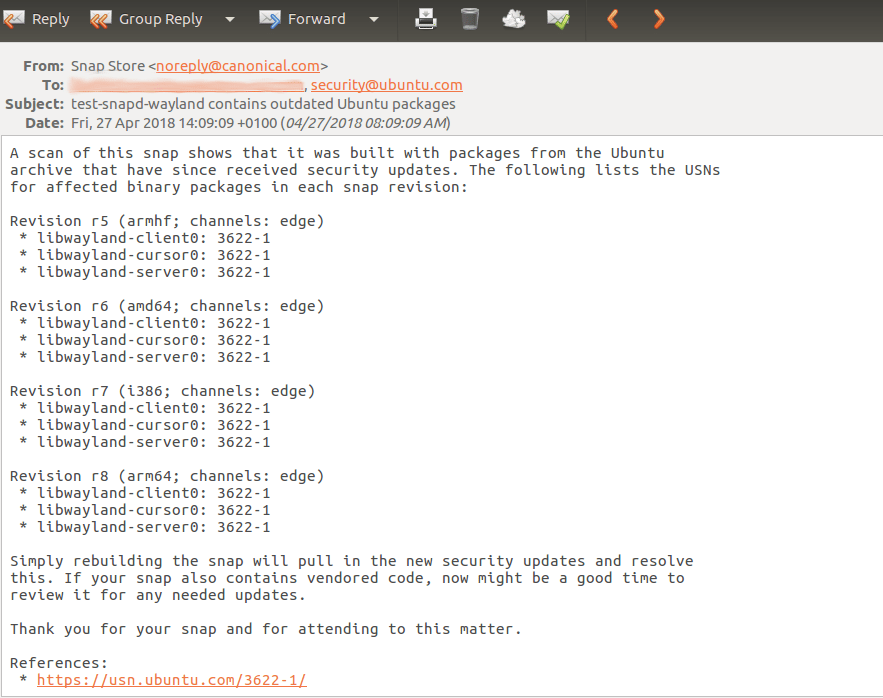
In this report, multiple revisions are flagged because they are the current revision for the architecture by channel. The reference section aggregates links to the Ubuntu Security Notice website. Vendored code refers to code which is pulled directly from upstream sources, for example, code that is pulled directly from the project’s source code repository (e.g. Github).
As a snap publisher, you can opt-in to receiving these notifications by including a snap/manifest.yaml in your snap. The manifest will be generated for you in the following cases:
- snaps built with SNAPCRAFT_BUILD_INFO=1 will have a snap/manifest.yaml inserted into the snap before the ‘snapcraft pack’ step.
- any snaps built on Launchpad will have SNAPCRAFT_BUILD_INFO=1 set automatically.
Once a day, the service examines snaps that have manifest.yaml files for their currently published channels/tracks and checks whether USNs have been issued for the versions of the staged packages in the snap. If any snap revisions are affected, the tool will generate a report to send via email. By default, the report will be emailed to the publisher’s registered email address and the uploader’s registered email address. It is important to note that even when a snap includes a staged package containing a vulnerability, it does not mean that the snap is necessarily affected by the vulnerability. The developer will need to have a look at the vulnerability to determine whether and how the snap is affected. This service is therefore a one-time notification service and will not continue to nag the publisher about unfixed vulnerabilities. The service records the emails that have already been sent for USNs by revisions of the snap and will only send an email for a particular report once. The publisher will receive a new report only if something has changed in the report, for example, a new USN affects the snap or a new affected revision of the snap is published.
Since this is a new service, we would love to hear feedback. If you discover any issues or have any requests, please report them in the forum using the ‘store’ tag or at https://bugs.launchpad.net/review-tools/+filebug.



